9 min read
Terrorist Use of End-to-End Encryption: Insights from a Year of Multi-Stakeholder Discussion
Adam Southey Jan 11, 2023 10:04:19 AM
Summary
In September 2021, Tech Against Terrorism published a landmark report entitled Terrorist Use of E2EE: State of Play, Misconceptions, and Mitigation Strategies on a topic which has become a central area of concern for policymakers and tech companies alike. Both are charged with stopping the exploitation of this technology while upholding commitments to privacy and human rights. Our report provides a comprehensive overview of the risks and mitigation strategies related to terrorist and violent extremist use of online services offering end-to-end encryption, with a focus on communication services.
Our report on terrorist and violent extremist use of E2EE was published as the starting point of a necessary conversation on risk mitigation strategies which compromise neither encryption nor the right to privacy. Both in the report and the subsequent discussion, we mapped out risk mitigation strategies, for both service providers and law enforcement, that would not require “breaking” encryption. By using the term “breaking” encryption, we refer equally to all calls to counter terrorist and illegal use of encryption through the systematic monitoring of encrypted content (including pre-encryption) or providing direct access to encrypted content to third parties, as well as any other mitigation strategies that would undermine the inherent privacy of encryption. For an overview of policymakers’ calls to rein in encryption, please see Part 1.8 “Policymakers Calls for Access to and Traceability of E2EE” of Tech Against Terrorism’s report on terrorist use of E2EE.
To facilitate this essential discussion, Tech Against Terrorism organised three workshops in 2022 with a view to identifying the strategy which could balance the objectives of safeguarding encryption, and the fundamental right to privacy, with countering terrorism and violent extremism. Throughout the year we convened online service providers, cryptographers, policymakers, counterterrorism experts, and digital rights advocates in a series of workshops which culminated in a panel held on the fringe of the 77th UN General Assembly. We structured the discussions according the outline of Tech Against Terrorism’s report on E2EE, and each event was dedicated to a specific sub-topic:
- State of play of the threat
- Existing policy responses
- Mitigation strategies
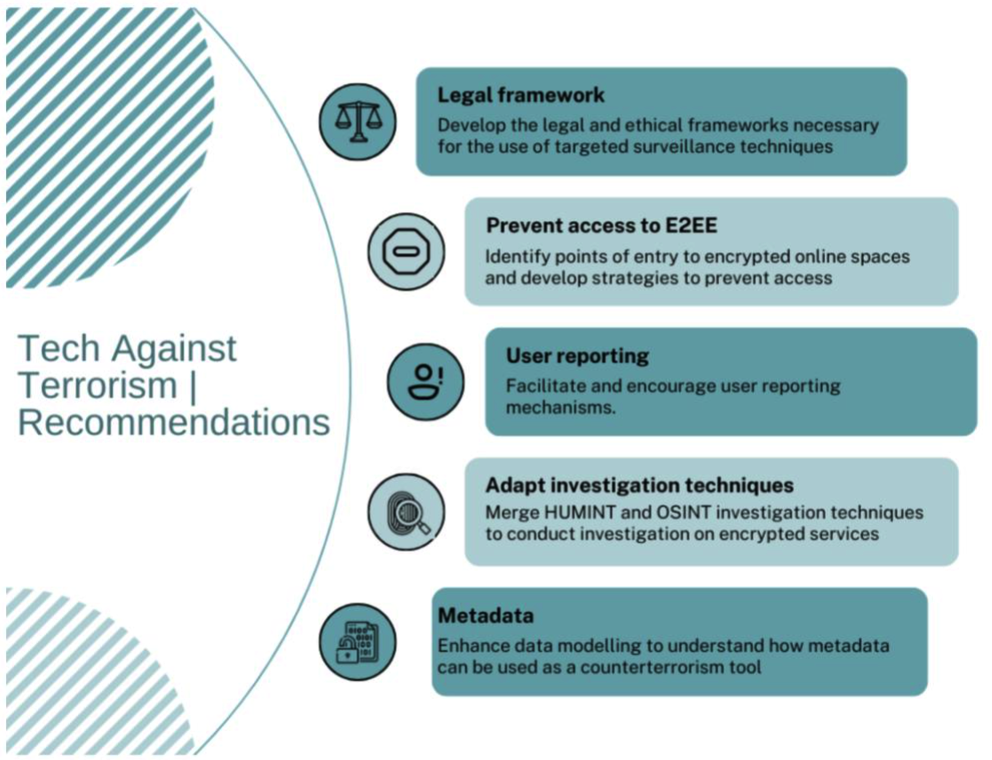
EXECUTIVE SUMMARY AND RECOMMENDATIONS
- We cannot ignore the realities of terrorist and violent extremist use of E2EE services, and in particular their use for operational purposes and attack planning. To adequately counter terrorist and violent extremist use of E2EE, it is critical to understand the role of E2EE in the wider threat landscape and how it links to terrorist and violent extremist use of other, non-encrypted, online services.
- Existing mitigation strategies which safeguard encryption should be further developed by online service providers, law enforcement, and policymakers. Use of non-encrypted data, targeted surveillance techniques, and the prevention of access to encrypted services are both easily deployable and scalable.
- Online service providers should take the lead on developing resilient mitigation strategies focused on the early prevention and detection of terrorist and violent extremist use of their services. Metadata are available to detect terrorist and violent extremist use, and measures can be introduced to limit or prevent terrorist and violent extremist users from accessing encrypted services in the first place.
- Online service providers and law enforcement bodies should consider developing mitigation strategies focusing on the link between encrypted and public online spaces. Tech Against Terrorism’s Terrorist Content Analytics Platform (TCAP), for instance, can be used to report join links shared on non-encrypted platforms.[mfn]For more on the Terrorist Content Analytics Platform, visit the website. https://www.terrorismanalytics.org/
- Law enforcement should adapt to the evolution of the online space and focus on targeted monitoring techniques to counter terrorist and violent extremist use of encrypted spaces. Human intelligence techniques (HUMINT) can be adapted and used to conduct investigations into encrypted channels.
TERRORIST AND VIOLENT EXTREMIST USE OF E2EE SERVICES
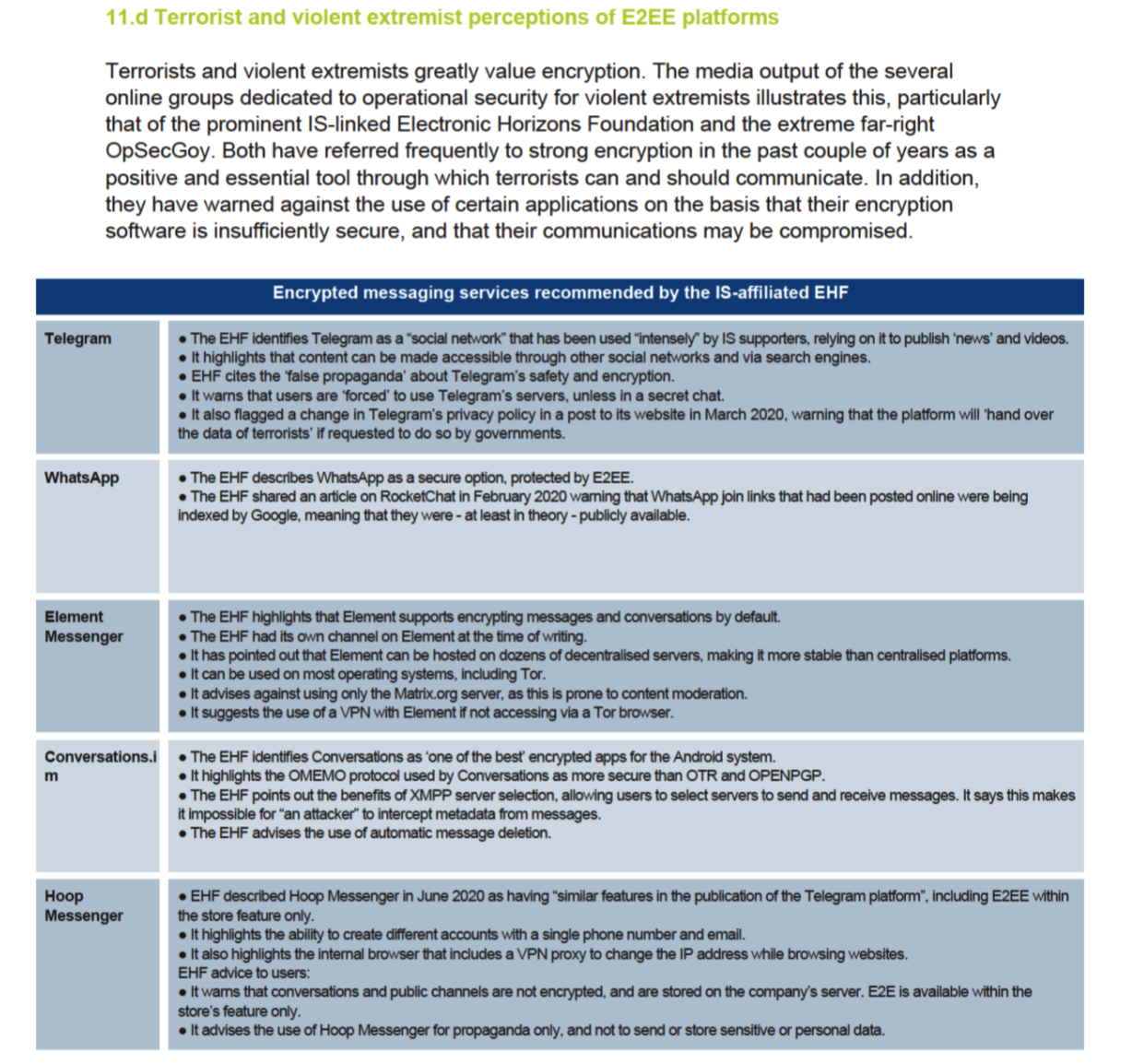
Terrorist and violent extremist use of encrypted services is a reality and a significant feature of the online threat landscape that cannot be ignored. For more on platform functionalities see our report Terrorist Use of E2EE: State of Play, Misconceptions and Mitigation Strategies. E2EE affords users enhanced security and privacy and is used by terrorists and violent extremists for operational purposes, including internal communications, training, attack planning and coordination. E2EE poses significant challenges for detecting and monitoring terrorist and violent extremist activity, since most mitigation strategies capable of deployment on public-facing online services are of limited use in encrypted spaces. The main barrier to widespread terrorist and violent extremist use of encryption remains its limited audience reach, which restrains its use for strategic purposes.
Concerns over the use of E2EE for terrorist and violent extremist purposes have motivated calls to break encryption by providing law enforcement with general access to encrypted content, or by introducing the proactive and systematic scanning of all encrypted content. Policymakers have also been calling for the systematic scanning of content shared via encrypted services. However, these calls have been motivated by the objective of countering the dissemination of child sexual abuse material online, rather for the purposes of counterterrorism. Encryption experts, digital rights advocates, and service providers agree that the systematic surveillance of encrypted content is not technically feasible without compromising the security and privacy of all users.
LOOKING FORWARD: MITIGATION STRATEGIES SAFEGUARDING ENCRYPTION
The use of tools to conduct systematic scanning and surveillance of encrypted services may seem an appealing solution to counter terrorist and violent extremist use of E2EE. However, they fall short of their stated aims. They are resource intensive, difficult to implement at scale, and present significant risks of misuse, including abuse by criminal actors and authoritarian states. Terrorists and violent extremists are also known to migrate from platform to platform once restrictive measures have been applied, and would move to more secure, and non-compliant, platforms were encryption to be compromised.
Mitigation strategies must focus on a combination of proactive and reactive measures around non-encrypted data and entry points. These include enhancing user empowerment through better user-reporting processes and proactive interventions at the entry points, such as by tracking the join links to E2EE protected channels. Equally, mitigation strategies should include proactive detection measures, such as metadata analysis and targeted surveillance – both of which are limited in their enforcement of the right to privacy but are fundamentally compatible with E2EE. Tech Against Terrorism recommends the following mitigation strategies be adopted by both online service providers, policymakers, and law enforcement bodies.
- Encryption centred policy responses
Recommendation 1.
E2EE service providers should include explicit prohibition of terrorism and violent extremism in their content standards. Such provisions should develop their counterterrorism framework, and how it safeguards encryption, in a dedicated policy.
Service providers can and should develop the necessary counterterrorism frameworks, starting with a clear policy prohibiting terrorist and violent extremist use of their services as well as the sharing of related content. Terrorists and violent extremists’ perception of platforms’ willingness and capacity to moderate their services can be pivotal in their decision to establish themselves on a platform. The more a platform appears to be stable, meaning not taking actions against terrorist and violent extremist content, the more likely it is to be exploited. Conversely, a platform that takes a strong and public counterterrorism stance, acting against prohibited conduct with technically feasible measures, will deter terrorists and violent extremists.
Recommendation 2.
Policymakers should consult with service providers, cryptographers, counterterrorism experts, and digital rights advocates to develop legal responses. These responses to terrorist and violent extremist use of E2EE should safeguard encryption and meet their stated aims.
Recommendation 3.
Policymakers should ensure that there is a clear legal framework that considers the ethical and legal questions surrounding the countering of terrorist use of E2EE.
Policymaker calls for lawful access to encrypted content have led to an increase in legislative proposals that directly or indirectly impact E2EE and which threaten the fundamental right to privacy and the security of all users but with no proven benefits. In the future, policymakers should ensure that legal responses to terrorist use of E2EE are developed in consultation with service providers and cryptographers to ensure that E2EE will not be negatively impacted. Digital rights advocates should also be consulted to ensure that the necessary safeguards are in place for users whose rights have been infringed. If policymakers opt to encourage the use of metadata to detect terrorist use of E2EE services, or lawful hacking to permit digital investigation, they should also ensure that the ethical and legal questions raised by these options are answered via a clear legal framework.
- Preventing access to encrypted services
Recommendation 4.
Service providers should work with law enforcement and counterterrorism experts to identify and block access to encrypted channels associated with terrorists and violent extremists.
Recommendation 5.
E2EE service providers should introduce obstacles to terrorist and violent extremist access to their services. Such obstacles must include limits on the use of joining links.
Terrorist and violent extremist use of E2EE is a part of the broader online threat landscape and should be understood as such to develop efficient mitigation strategies. In parallel with exploitation of E2EE services, terrorists and violent extremists rely on the usability and audience reach of public-facing or unencrypted platforms for recruitment and propaganda. Terrorists and violent extremists rely on outlinking from un-encrypted online spaces to shift followers towards secure and encrypted channels of communication. Preventive measures should focus on identifying and blocking these entry points to E2EE services and should focus on early interventions in particular. For instance, Tech Against Terrorism’s research shows that join links shared on unencrypted channels play a critical role in driving terrorist and violent extremist users to encrypted spaces. Encrypted service providers should limit the use of join links in order to disrupt and prevent access to their platforms. The Terrorist Content Analytics Platform can support with this by alerting the encryption provider to join links shared on unencrypted spaces. Service providers should also work with counterterrorism experts to identify those channels, groups, and email addresses which are used by terrorists and violent extremists and promoted in non-encrypted spaces.
- User reporting
Recommendation 6.
E2EE service providers should ensure users’ easy access to reporting mechanisms. Providers should also make available more accessible resources for users about the reporting processes.
Recommendation 7.
Service providers should collaborate with counterterrorism researchers to investigate ways in which user reporting can be used as part of a broader mitigation strategy for terrorist and violent extremist use of E2EE services.
User reporting is an easily deployable and encryption-compatible solution which can identify and counter terrorist and violent extremist use of E2EE services. There are different reporting solutions. (For a visualisation of E2EE services user reporting mechanisms, see section (18)(a) on Reactive content moderation and E2EE of Tech Against Terrorism’s report on terrorist use of E2EE, which outlines how to ensure the authenticity of the message reported without compromising encryption protocols.) For instance, encryption providers can offer in-app user reporting features relying on message franking, which allows users to flag a message without giving the encryption and decryption keys to the service provider, or provide a dedicated email address for abuse reporting. Whilst this is less direct than in-app flagging, users could still screenshot messages and send them via email to report content. Whilst the consensual sharing of terrorist content on E2EE platforms poses a challenge to E2EE service providers, its emphasis on empowering the user to flag content without posing a threat to users’ privacy highlights the overall utility of user reporting and its important role in any mitigation strategy.
- Use of available metadata
Recommendation 8.
Service providers should build metadata modelling. Collaboration with counterterrorism experts is required to understand the potential of metadata for counterterrorism.
Recommendation 9.
Law enforcement, service providers, and counterterrorism experts should collaborate to identify terrorist and violent extremist patterns of behaviours on E2EE services using metadata.
Recommendation 10.
Policymakers should provide a clear legal framework on the use of metadata as a counterterrorism tool. These frameworks must include the necessary safeguards for the right to privacy.
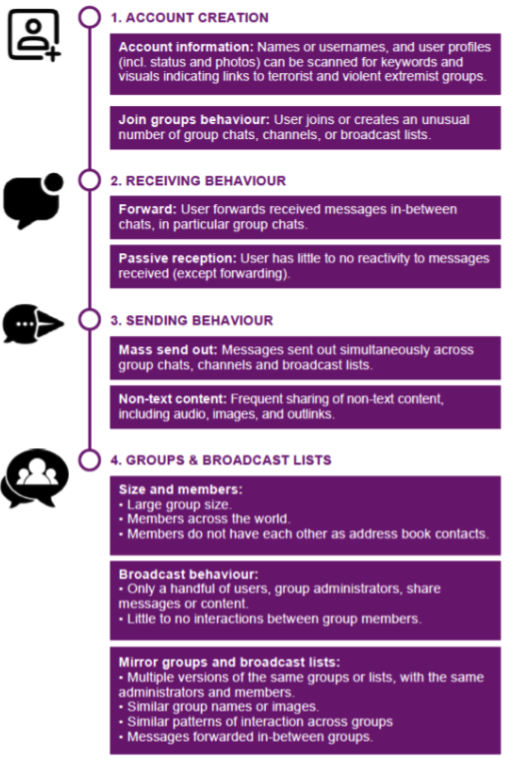
Metadata can support tech companies to detect terrorist use of their services by providing signals of affiliation and behaviour that are not encrypted. For instance, usernames and profile pictures can be scanned to detect signs of terrorist and violent extremist affiliation and support. These can be associated with patterns of use, which can often be built using non-encrypted data for the purpose of identifying terrorist and violent extremist networks on encrypted services. Equally, metadata can provide intelligence to support digital investigations without accessing encrypted content. However, more research is necessary to understand the potential of metadata as a counterterrorism tool, including into what exact types of metadata are of use for simply detecting terrorist conduct, rather than for the purpose of compiling criminal evidence. Data modelling is also required to understand how metadata can be deployed at scale.
Excerpt from Part 3 “Strategies for Risk Mitigations” of Tech Against Terrorism’s report on terrorist use of E2EE.
- Considering targeted surveillance solutions
Recommendation 11.
Law enforcement should adapt HUMINT investigation techniques to the online landscape. Passive and active monitoring should be adapted for use within encrypted spaces without breaching encryption protocols.
Recommendation 12.
Law enforcement should detail in which circumstances targeted surveillance, in particular lawful hacking, can be beneficial for investigations. There must also be clarity on what level of cooperation from service providers would be valuable.
Recommendation 13.
Policymakers should provide a clear legal framework delineating targeted surveillance techniques, with respect for the rule of law, due process, and user rights. This should specify when and how targeted surveillance is permissible, as well as what can be reasonably expected of tech companies – with consideration for users’ right to privacy and overall security of the service.
Encryption does impact the monitoring of terrorist and violent extremist activities online for the purposes of criminal investigations. However, targeted surveillance techniques exist and can be adapted to conduct investigations without compromising encryption protocols. By merging open-source intelligence (OSINT) and HUMINT, lawful monitoring can be conducted on encrypted services. Passive monitoring can be done both via the use of publicly available information to track terrorist and violent extremist networks operating in both public and private online spaces, focusing on the points of entry to encrypted channels. Passive monitoring can also be conducted on certain encrypted spaces, without substantial engagement with the different participants in the communication channel. Furthermore, law enforcement bodies can undertake participative monitoring by going undercover online as they would have done offline.
Lawful hacking is also an investigative tool warranting further development since it can permit law enforcement access to a suspect’s device and does not compromise the broader encryption protocols by providing blanket backdoor access to encrypted content. Tech Against Terrorism provides an overview of lawful hacking techniques in section 19 of our report entitled Going Beyond the Encryption Debate. However, whilst different lawful hacking techniques exist, all pose difficult questions concerning the threshold of suspicion required to justify the practice, including the level of cooperation required from service providers and whether technical vulnerabilities exploited are notifiable to those providers; the safeguards to limit interference with users’ rights; and the assessment of a measure’s proportionality to its objective. The answers to these questions must be found if lawful hacking is to be conducted with respect for the rule of law and due process.
- News (240)
- Counterterrorism (54)
- Analysis (52)
- Terrorism (39)
- Online Regulation (38)
- Violent Extremist (36)
- Regulation (33)
- Tech Responses (33)
- Europe (31)
- Government Regulation (27)
- Academia (25)
- GIFCT (22)
- UK (22)
- Press Release (21)
- Reports (21)
- US (20)
- USA (19)
- Guides (17)
- Law (16)
- UN (15)
- Asia (11)
- ISIS (11)
- Workshop (11)
- Presentation (10)
- MENA (9)
- Fintech (6)
- Threat Intelligence (5)
- Webinar (5)
- Propaganda (3)
- Region (3)
- Submissions (3)
- Generative AI (1)
- Op-ed (1)
Summary Report – Terrorist Exploitation of E2EE: Policy Responses
