Reader's Digest – 27 May 2022
Our end-of-month review of Tech Against Terrorism's work, providing updates on the Open-Source Intelligence (OSINT), Research, and Policy Advisory and Response (PAR) teams.
Job Alert!
- We are looking for a Junior Policy Analyst to join our Policy Advisory and Response (PAR) team. This role will focus on our Mentorship Programme and will involve working directly with tech platforms to get involved in strengthening online counterterrorism approaches across the tech eco-system. This is suited for early career candidates with an interest in counterterrorism and tech policy. Find out more and apply here.
Tech Against Terrorism Updates
- Our Senior Research Analyst, Anne Craanen, presented at the Global Network on Extremism and Technology (GNET) Second Annual Conference. She showcased the Terrorist Content Analytics Platform and presented on our recent Transparency Report.
- Anne Craanen also presented at the TextGain conference on Gamification, Hate Speech and Radicalization. Anne presented on the gamification of terrorism and methods to counter this type of terrorist content.
- Anne Craanen also attended Hedayah’s International Countering Violent Extremism Research Conference where she presented on adversarial shifts and terrorist operated websites. She also co-moderated a side panel with GIFCT on ethics when conducting P/CVE research and OSINT.
- We published our summary report from our roundtable on “Terrorist Use of E2EE Services: Policy Responses.” The report considers the current policy responses to end-to-end encryption, and highlights the complexities to policy responses in terms of jurisdiction, fundamental right to privacy, and safeguards against abuse. It concludes with risk mitigation strategies for tech companies and innovative law enforcement investigation techniques.
Research Team Update
- On 14 May, an attacker carried out a shooting in Buffalo, New York, USA, killing 10 people and injuring 3 others. The attack perpetrator released a 180-page manifesto prior to the attack, and livestreamed the attack on Twitch. Twitch removed the livestream within 2 minutes of the attack beginning.
- The Research team’s analysis of both the attacker’s livestream and manifesto indicated that this content was instructional in nature and promotional of further violence against non-white communities. We were especially concerned about the repackaging of this content by online far-right networks, who have repurposed and reshared both pieces of content for propaganda purposes.
- On 15 May, the New Zealand Classification Office initially classified the attacker’s manifesto as objectionable, followed by the livestream video of the attack on 16 May, criminalising the possession and distribution of both of these publications. In line with the legal basis of the TCAP’s Inclusion Policy, the TCAP began alerting the Buffalo attack perpetrator’s manifesto and livestream to tech companies on 17 May. This decision was based on our assessment of the threat posed by the rapid dissemination of this content whilst closely considering compatibility with the rule of law.
- The TCAP also alerts the Norway attacker’s manifesto and material produced by the Christchurch attack perpetrator, all publications which have been previously banned by democratic governments and which were referenced as inspiration in the Buffalo attacker’s manifesto.
Open-Source Intelligence (OSINT) Team Update
- Over the past weeks, the Open-Source Intelligence (OSINT) team has been monitoring the spread of content relating to the May 14 Buffalo shooting. Since adding the livestream and manifesto to the TCAP, we have identified 133 URLs and made 62 alerts to 7 tech platforms.
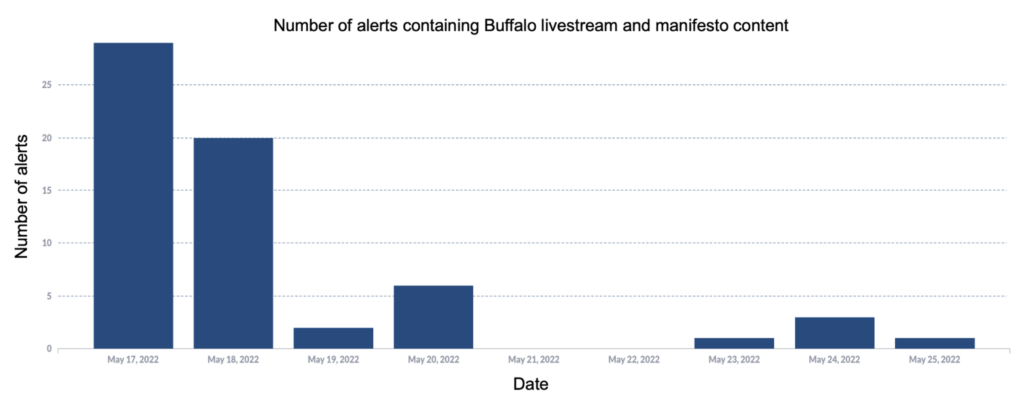
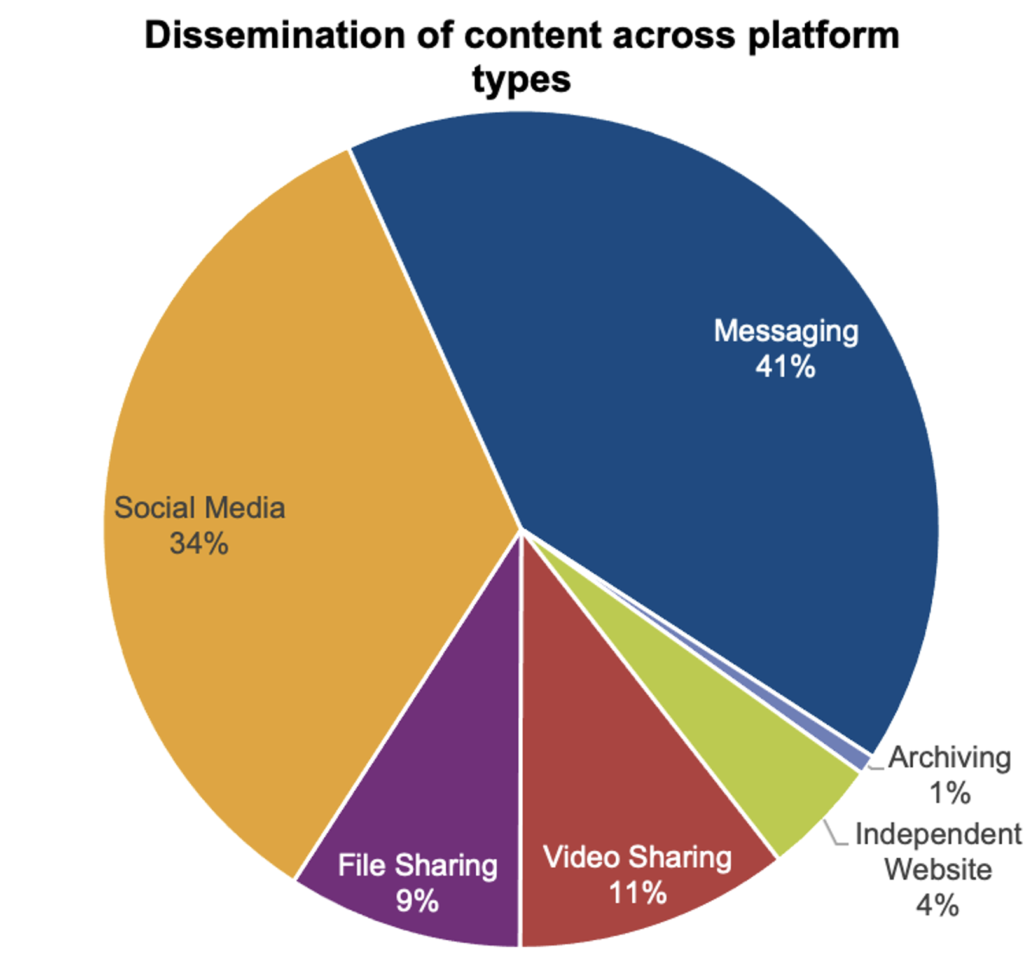
- Our analysis of the spread of content shows that while Twitch suspended the livestream within 2 minutes of the attack starting with 22 viewers, copies of the livestream have since been widely circulated by far-right violent extremist supporter networks. Copies of the attack perpetrator’s manifesto have also been widely shared, primarily through outlinks on popular far-right channels. The graph below shows the distribution of URLs containing manifesto and livestream content, sorted by platform type.
Policy Advisory and Response (PAR) Team Update
- Over the month of May, the Policy Advisory and Response (PAR) team has focused its efforts on human rights and meaningful transparency, working to expand the scope of the support we provide to the global tech sectors and policymakers in creating resilient yet rights-respecting and transparent online counterterrorism responses.
- We published our assessment of New Zealand’s first Digital Violent Extremism Report, which shows that New Zealand’s report includes almost all information and metrics recommended by Tech Against Terrorism in our Guidelines on Transparency Reporting on Online Counterterrorism Efforts. Government transparency is vital to ensure that governments are accountable to their citizens and to internet users, and we encourage all government to report on their online counterterrorism efforts in line with our Guidelines.
- The PAR team has also been working on consolidating its different resources on transparency and human rights into a consolidated framework to consolidate the different avenues of support we provide to tech companies. Watch out for the published framework!
For any questions, please get in touch via:
contact@techagainstterrorism.org
- News (239)
- Counterterrorism (54)
- Analysis (52)
- Terrorism (39)
- Online Regulation (38)
- Violent Extremist (36)
- Regulation (33)
- Tech Responses (33)
- Europe (31)
- Government Regulation (27)
- Academia (25)
- GIFCT (22)
- UK (22)
- Press Release (21)
- Reports (21)
- US (20)
- USA (19)
- Guides (17)
- Law (16)
- UN (15)
- Asia (11)
- ISIS (11)
- Workshop (11)
- Presentation (10)
- MENA (9)
- Fintech (6)
- Threat Intelligence (5)
- Webinar (5)
- Propaganda (3)
- Region (3)
- Submissions (3)
- Generative AI (1)
- Op-ed (1)
