4 min read
Summary Report: Assessing the Threat of Terrorist Exploitation of E2EE services and Existing Responses
Adam Southey Mar 21, 2022 4:27:53 PM
On 16 February, Tech Against Terrorism organised a roundtable discussion on “Assessing the threat of terrorist exploitation of E2EE services and existing responses.” This event marked the launch of a three-part roundtable series on assessing and countering terrorist use of end-to-end encrypted (E2EE) services, aiming to highlight risk mitigation strategies that safeguard privacy and security. This session saw participation from counterterrorism experts, digital rights advocates, as well as government and tech sector representatives.
Key insights from the roundtable:
- All participants agreed on the importance of safeguarding encryption whilst recognising the need to find a balanced solution to counter terrorist use of E2EE.
- Counterterrorism experts highlighted the necessity to contextualise terrorist use of E2EE within the broader terrorist online landscape in order to properly assess and counter the threat.
- The use of metadata analysis to detect and investigate terrorist use of E2EE, though often considered less privacy intrusive than content analysis, raises important legal and privacy questions that need to be considered.

Threat assessment: terrorist use of E2EE
The threat assessment provided by Tech Against Terrorism and ExTrac highlighted the need to situate terrorist exploitation of E2EE within the broader online terrorism threat landscape. Experts agreed that E2EE is not a decisive factor for terrorist groups when opting to use a specific platform, and that terrorist actors use E2EE in combination with other public and/or unencrypted platforms. However, experts highlighted that E2EE is often preferred by terrorist actors for operational purposes and is often used ahead of terrorist attacks. Experts also noted that terrorists’ perception of a platform plays into the extent to which they opt to use it.
Terrorist use of E2EE: Mitigation strategies and metadata analysis[mfn]Metadata is the bulk information relating to a users’ information and communications behaviour1 that usually contains descriptive information about other data.1 This metadata, or non-content data, consists of “outside the envelope” information, such as sender and receiver identification, IP address, basic subscriber information, date, time, and location data.1 Thus, this data is information that service providers can observe through the provisioning of services: when, how frequently, how long, and with whom users are communicating. See: United Nations Office on Drugs and Crime – UNODC (2018), Privacy, investigative techniques and intelligence gathering; and Woods Andrew (2017), Encryption Substitutes, Hoover Working Group on National Security, Technology, and Law, Aegis Series Paper No. 1705.[/mfn]
Participants highlighted existing efforts from tech companies in identifying and countering terrorist use of E2EE. Tech platforms explained measures they take to prevent illegal activity of their services whilst safeguarding their commitment to encryption. Tech sector representatives emphasised unencrypted metadata sharing and termination of accounts used by terrorist actors as possible options to cooperate with law enforcement and counter terrorist use of E2EE. Experts and participants also discussed the different content moderation strategies that can be used to detect terrorist and criminal use of E2EE, with a focus on drawing a distinction between analysis of content and of metadata.
Using metadata to detect signs of association with a terrorist organisation
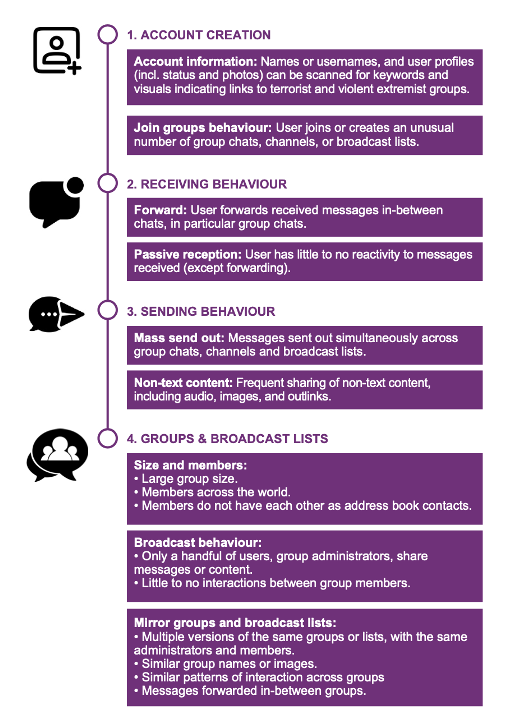
Metadata can be used by encrypted service providers to detect behavioural signs to identify terrorist networks exploiting E2EE services, in particular for strategic purposes (including propaganda and content dissemination).
Source: Terrorist Use of E2EE: State of Play, Misconceptions, and Mitigation Strategies, Tech Against Terrorism, 2021.
Metadata analysis was the mitigation strategy discussed in most depth. As outlined in Tech Against Terrorism’s report,[mfn]Part 3, Section 17 of the report on “Identifying Patterns of Criminal Use – Metadata Analysis”.[/mfn] metadata analysis is often perceived as less privacy intrusive than solutions that would require access to content, but that is not always necessarily so. In particular, metadata analysis can be used by tech platforms to detect terrorist networks on E2EE services and by law enforcement when conducting online investigations. However, participants also noted several downsides to using metadata analysis, including doubts regarding its efficacy and questions about data privacy. Policymakers and digital rights advocates highlighted that metadata is arguably as sensitive as content data and raises major privacy challenges. They stressed that metadata analysis for counterterrorism purposes should not encourage platforms to expand their metadata collection, which would lead to a surge in platforms’ collecting of personally identifiable information and raise questions of legal liability in collecting such information. Tech platforms stressed that more research is required in order to understand how metadata analysis could moderate terrorist content while preserving strong E2EE.
Looking forward: Policy framework for responding to terrorist use of E2EE
The threat assessment and ensuing discussion about mitigation strategies highlighted the necessity of shifting the debate on countering terrorist exploitation of E2EE: from an encryption debate that mistakenly places online and offline security in direct opposition to each other, to a broad safety paradigm that includes aspects of prevention, detection, and countering at different stages of risks. Beyond the question of metadata analysis, participants thus raised the question what can be done when replacing terrorist use of E2EE in the broader online threat landscape to prevent migration to prevent terrorists and violent extremist from migrating to encrypted services. Participants also discussed law enforcement investigations, including the need to increase resources and skill to merge human intelligence (HUMINT) with open-source intelligence (OSINT) to adapt investigation techniques to the online space without creating a backdoor to encryption.
The discussion also highlighted the need to address the different legal and ethical questions that surround possible risk mitigations strategies to detect and counter terrorist use of E2EE services, in particular regarding identifying a solution that does not undermine online security or users’ fundamental rights. These questions will be at the core of the second roundtable of the series, which will discuss “Policy responses to terrorist use of E2EE” and focus on the legal framework underpinning tech sector and law enforcement responses to terrorist use of E2EE.
BACKGROUND TO THE SERIES
Strong encryption is the backbone of data security and online privacy. Internet users realise this, and tech companies, in particular messaging services, have increased their offering of E2EE services in response to user demand for privacy. The increased popularity and widespread use of E2EE has led to government and law enforcement concerns over terrorist exploitation of encrypted communication channels, and many governments are exploring ways to grant law enforcement access to encrypted communications, or to introduce obligations for service providers to monitor these communications.[mfn]For instance, the United Kingdom and Australia have both passed acts governing the possibility for law enforcement to request access to normally encrypted data (respectively the Investigatory Powers Act of 2016, and the Assistance and Access Act of 2018), The European Union has been calling on tech companies to be able to detect certain types of illegal content, notably child sexual abuse material, on encrypted services with the Strategy for a more effective fight against child sexual abuse (July 2020). In certain jurisdictions that have recently passed regulation on illegal and harmful content, or are in the process of passing one, requirements for platforms to counter the dissemination of illegal and harmful content also applies to platforms offering E2EE. For a more complete overview of governments’ call for access to or monitoring of encrypted communications, please see Section 8 of our report on terrorist use of E2EE.[/mfn] This has in turn caused objections from both tech companies and digital rights advocates, as well as security experts.
The roundtable series is being organised following the publication of our landmark report on “Terrorist use of E2EE: State of play, misconceptions and mitigations strategies”, which provides a comprehensive overview of the risks and mitigation strategies related to terrorist and violent extremist exploitation of E2EE services and outlines recommendations for governments and tech companies. We are organising these roundtables to facilitate constructive dialogue and build trusted relationships between tech platforms, governments, and law enforcement, as well as counterterrorism and digital rights experts to outline a pathway to countering terrorist use of E2EE without “breaking” encryption or violating privacy.
- News (240)
- Counterterrorism (54)
- Analysis (52)
- Terrorism (39)
- Online Regulation (38)
- Violent Extremist (36)
- Regulation (33)
- Tech Responses (33)
- Europe (31)
- Government Regulation (27)
- Academia (25)
- GIFCT (22)
- UK (22)
- Press Release (21)
- Reports (21)
- US (20)
- USA (19)
- Guides (17)
- Law (16)
- UN (15)
- Asia (11)
- ISIS (11)
- Workshop (11)
- Presentation (10)
- MENA (9)
- Fintech (6)
- Threat Intelligence (5)
- Webinar (5)
- Propaganda (3)
- Region (3)
- Submissions (3)
- Generative AI (1)
- Op-ed (1)