Headline news
Tech Against Terrorism held a virtual meeting for its Advisory Group and Experts Committee on 27 May. This meeting followed up on the meeting held last year at the United Nations Counter Terrorism Directorate (UN CTED) headquarters in New York during the UN General Assembly week. In this month's meeting Tech Against Terrorism provided an update on its work in 2020 around its core activities around outreach, knowledge-sharing, and practical support for the tech sector. The meeting saw opening remarks from ASG Michele Coninsx, Executive Director of UN CTED. Tech Against Terrorism would like to express its gratitude to our stakeholders attending this meeting, including UN CTED, the governments of Canada, United States, United Kingdom, Switzerland, and Jordan, the European Commission, Europol, the Commonwealth, Facebook, Google, Access Now, VOX-Pol, and Swansea University.
On 5 May Tech Against Terrorism contributed to a virtual EU Internet Forum meeting on far-right violent extremist and terrorist use of the internet, sharing insights from our research on far-right terrorist use of online platforms. This meeting was the first EU Internet Forum meeting addressing far-right violent extremism and terrorism.
Our latest webinar in partnership with the Global Internet Forum to Counter Terrorism (GIFCT) addressed the topic of the tech sector and law enforcement engagement in countering terrorist use of the internet. Opened by Courtney Gregoire, Chief Safety Digital Officer at Microsoft, the webinar saw presentations from Jessica Marasa, Law Enforcement Response Manager at Twitch, Stephanie McCourt, Trust & Safety Outreach Lead at Facebook, Dina Hussein, Counter Terrorism and Dangerous Organisations Policy Manager at Facebook, as well as from the EU Internet Referral Unit at Europol. The webinar aimed to increase understanding of each sector’s online counterterrorism practices, with the tech sector representatives sharing insights on their companies’ work on law enforcement collaboration and digital evidence.
If you wish to access a recording of this webinar, please contact us on contact@techagainstterrorism.org
As we continue to develop the Terrorist Content Analytics Platform (TCAP) with support from Public Safety Canada, we organised a virtual meeting to update academics and expert researchers on progress in designing the platform, as well as on how the TCAP will support research on terrorist use of the internet. During this meeting Tech Against Terrorism’s Director, Adam Hadley, provided a background presentation on the TCAP and shared the results of the online consultation process we conducted in 2019. Our Product Manager, Tom Lancaster, also provided an overview on the development progress of the platform and on the TCAP Beta Program. This virtual meeting also saw remarks from Peter King, Independent Consultant on extremist media and Director at IbexMind, as well as from Alexander Corbeil, Research Advisor at Public Safety Canada. Dr. Shiraz Maher, Director at the International Centre for the Study of Radicalisation, provided introductory remarks on the Global Network on Extremism and Technology (GNET), which Tech Against Terrorism recently partnered with.
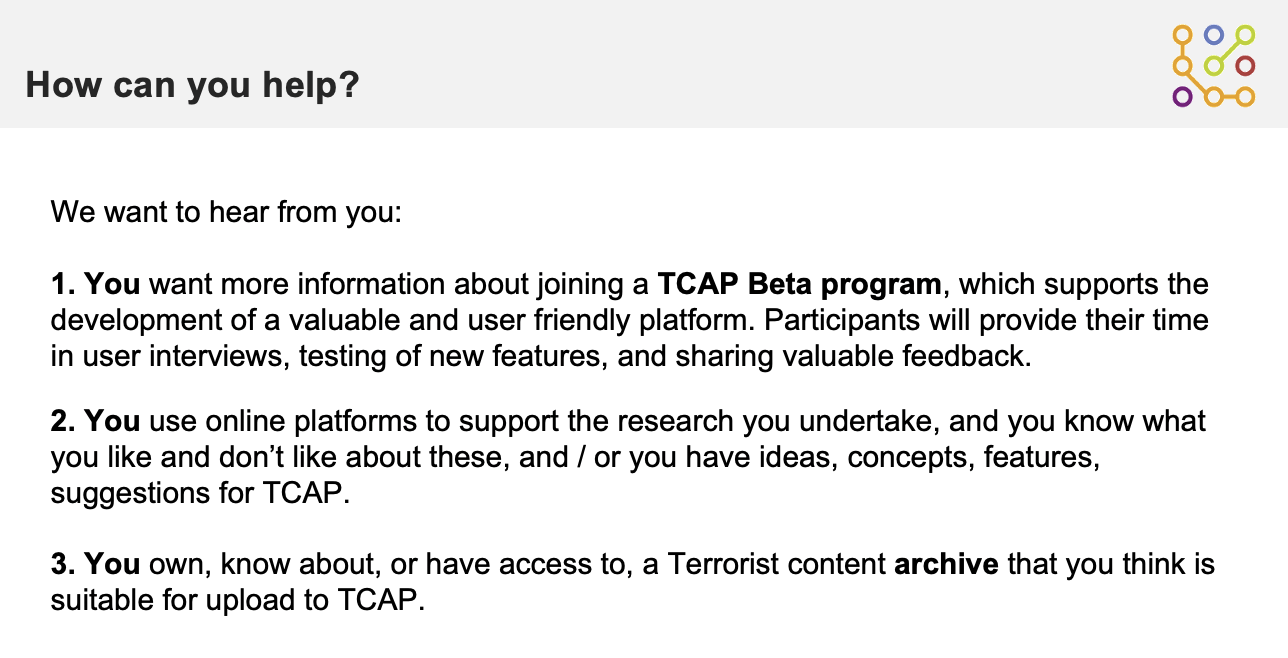
If you wish to take part in the TCAP Beta Program, or to contribute to the development of the TCAP, please send us an email at contact@techagainstterrorism.org
Season 2 of the Tech Against Terrorism Podcast is still going strong:
– In May we spoke about how terrorists and violent extremists are using gamificationwith Linda Schlegel, a Senior Editor at The Counterterrorism Group and a regular contributor for the European Eye on Radicalization, and Dr. Nick Robinson, an Associate Professor in Politics and International Studies at the University of Leeds.
– In the fourth episode of the season, we discussed the challenges of regulating the online sphere, with a particular focus on terrorist content. We spoke with two leading experts on this topic – Evelyn Douek, a Lecturer in Law and SJD Candidate at Harvard Law School, and Affiliate at the Berkman Klein Center for Internet & Society; and from Daphne Keller, Director of Platform Regulation at Stanford’s Cyber Policy Center.
In April, the US Department of State proscribed the Russian Imperial Movement as a specially designated global terrorist entity – the first time the US gives such a designation to a far-right violent extremist entity. Tech Against Terrorism welcomes this designation as it will help facilitate an improved tech sector response to online manifestations of far-right terrorism. We encourage states to use legal powers to promote rule of law through comprehensive terrorist designation lists. You can read our blogpost on this designation here.
What's up next?
Our monthly e-learning webinars in partnership with the GIFCT will continue this month with a webinar on intergovernmental organisations (IGOs) and their work countering terrorist use of the internet, during which we will hear from our partners in UN CTED and other international organisations. Following this, the webinar series will continue on the topics of:
– Tech platform accountability mechanisms – 15 July
– Implementing counter narrative programmes for smaller tech platform – 12 August
More information about the webinars and registration links will be shared shortly.
The Tech Against Terrorism Podcast’s exploration of terrorist and violent extremist exploitation of the internet will continue in June, with an episode on women’s engagement in terrorism and violent extremism online.
Don't forget to follow us on Twitter to be the first to known when our webinar registrations are opened, and when the next episode of the Tech Against Terrorism Podcast is released.
Tech Against Terrorism Reader's Digest - 29 May
Our weekly review of articles on terrorist and violent extremist use of the internet, counterterrorism, digital rights, and tech policy.
Tech policy
- EU privacy enforcer hits make-or-break moment: Two years after the introduction of the EU’s landmark General Data Protection Regulation (GDPR), Ireland’s data protection authority is facing mounting pressure from its European counterparts to enforce what has become a “de facto global standard” for online privacy across the world. Mark Scott dwells on this “make-or-break moment” for the Ireland’s Data Protection Commission: with many tech giants having international headquarters in Ireland, the country is on the frontline of GDPR enforcement. With Ireland expected to enforce significant fines for some tech giants, “almost a year after the enforcement actions were originally expected”, Scott analyses some of the factors that have slowed down the work of the data protection agency. These mainly include the important number of cases and having to work with an entirely new framework for privacy standards, as well as budgeting decisions when additional staff would be required to properly handle the mounting number of cases. (Scott, Politico, 23.05.2020)
- Facebook Messenger adds safety alerts – even in encrypted chats: Andy Greenberg examines Facebook’s new safety alerts feature that will inform users when receiving a message from potential financial scammers and child abusers. Based on machine-learning analysis of communications on Facebook Messenger, the feature will work through behavioural detection mechanisms based on metadata analysis. By using only metadata, this new feature will thus be compatible with end-to-end encryption (E2EE). Whilst the feature is for now mostly relevant for Facebook Messenger’s E2EE Secret Conversation features, it could help build up the platform’s response to the criticisms it has faced since announcing its plan to roll-out E2EE across its platforms announced in 2019. However Greenberg, in discussion with Alex Stamos (Director at the Stanford Internet Observatory, and former Facebook’s Chief Security Officer) concludes by stressing that this new feature is just a start, while Stamos argues that tech platforms should do more to monitor malevolent behaviours while protecting E2EE. (Greenberg, Wired, 21.05.2020)
- We need to fix GDPR’s biggest failure: broken cookie notices: In this article, Matt Burgess analyses one of the main effects on user experience resulting from the EU General Data Protection Regulation (GDPR): cookie consent notices. Present on most websites in Europe and asking users for permission to collect their information, cookie notices are presented in a variety of ways. The author argues that most, however, are designed to push users to accept all cookies. Burgess looks at how these notices are designed and implemented, and on the legal obligations behind them – underlining the lack of enforcement/penalties for websites not applying by the rules. He concludes by stressing that most researchers working on cookie notices speak in favour of increased GDPR regulation, and for websites to “use privacy by design and by default,” as stated by Access Now’s Estelle Massé in the article. (Burgess, Wired, 28.05.2020)
Terrorism and violent extremism use of the internet
- The internet and lone wolf terrorism in India: In this piece, Kabir Taneja and Prithvi Iyer argue for a better understanding of the crucial role of the internet in “lone wolf” attacks within the Indian domestic context. The authors argue that it is an important enabling link that has been understudied thus far, especially as the country has witnessed a number of individual shooters with no apparent links to a terror network following the announcement of the Citizenship Amendment Act (CAA). Taneja and Iver thus dwell on how the internet acts as an enabling space of conversation between like-minded individuals: providing them with a knowledge of others’ activities, tactical support, and a validation of their ambitions. The authors also show how misinformation around acts of violence can serve to strengthen different believes by being framed to reinforce “a preferred political narrative”. They use the example of a 33 year-old who waved a gun at a police officer during an anti-CAA protest in Delhi. This man was portrayed as an employee of ruling Bharatiya Janata Party (BJP) on social media, whereas reports on the ground identified him as an anti-CAA demonstrator. Regardless of his actual political affiliation, this act was framed differently to fit different beliefs. Taneja and Iyer conclude by stressing that more discussion around internet and lone-wolf terrorism is required in India, no matter the ideology, especially as the spread of misinformation on social media can play an important role in reinforcing self-beliefs. (Taneja & Iyer, GNET, 26.05.2020)
Islamist terrorism
- Inside the Sisterhood Springing Jihadis From Jail: This article, written by Anne Speckhard and Molly Ellenberg, discusses women’s attempts to escape from Islamic State’s (IS) detention camps run by the Syrian Democratic Forces (SDF). Speckhard and Ellenberg found increasing evidence that fundraising campaigns are set up in Europe to fund the escape of female prisoners from these detention camps. One of these campaigns, “Justice for Sisters”, was found on Instagram with one of the accounts linked to an illicit phone within the Al Hol camp. The campaign seemed to have launched in Germany and uses online crowdfunding to raise money amongst European sympathisers. Another account used the encrypted messaging app Telegram as well as PayPal for the financial transactions. To avoid a takedown by PayPal, the campaigns were given fake names. However, Telegram picked up on this particular channel and shut it down. The accounts also contain IS propaganda, as some of the women are considered “die-hard women” longing for the return of the caliphate. This article concludes by underlining that if Western states do not repatriate their citizens, the SDF will need support to detain the prisoners securely. (Speckhard & Eerenberg, Daily Beast, 24.05.2020).
- Al Qaeda and ISIS had a truce in Africa - until they didn't: Whilst the Sahel region has largely been exempted from the Islamic State (IS) and al-Qaeda rift, recent developments have changed this. In this article, Jacob Zenn and Colin P. Clarke discuss how this has impacted the stronghold held by Jama'at Nasr al Islam Wal Muslimin (JNIM) in the Sahel region and thereby opening the door to a greater Islamic State in the Greater Sahara (ISGS') presence. Due to this shift, the groups are now operating in close proximity, which together with stricter oversight by IS over its foreign provinces, have led to all-out conflict between JNIM and ISGS. Whilst a struggle between terrorist organisations is often deemed to negatively affect the groups in question, this article warns otherwise. Drawing on research by Mia Bloom and Brian Philips, it argues that the ongoing feud between JNIM and ISGS may lead to outbidding between the groups, longevity of both groups’ survival, and eventually to the sabotage of the peace accords discussed and implemented in the region. (Zenn & Clarke, Foreign Policy, 26.05.2020)
Far-right violent extremism and terrorism
- The symbols and ideas of the radical right: why their opponents should be more informed: The use of online platforms is essential for far-right violent extremists to spread their ideologies. However, violent extremists are aware of the discriminatory, sometimes illegal, nature of their political aims and often communicate through “double-edged signs” to bypass moderation and continue spreading their messages by hiding their intended purposes. Whilst some of these signs have become rather known to the mainstream public to “signify a reactionary political project”, their meanings and origins often remain unknown to them. In this article, Dr John Richardson and Dr Matthias Wasser present some of the results of their recent report on the significant signs of the violent far-right (a CARR project commissioned by Facebook). Including some background information on some of the symbols presented in the report: such as the Wolfsangel, a symbol for neo-Nazi commitment; and an explanation into the DOTR/DOR (“Day of the Rope” and “Day of Reckoning/Retribution”) acronyms. Dr Richardson and Dr Wasser conclude with some recommendations for engaging with someone drawn to violent extremism ideas based on empathic listening and presenting alternatives view rather than passing a judgement, and on preventing those sharing violent extremist views from controlling the discussion when in a multi-person setting. (Dr Richardson & Dr Wasser, Connect Futures, 26.05.2020)You can read the full report by the Centre of Analysis of the Radical Right here
Counterterrorism
- UK government's new counter-terrorism bill: the key measures: Jamie Grierson discusses the measures under the UK’s new counter-terrorism bill. The article sums up the main tenets within the bill, including the new sentencing regime, which allows offenders to be sentenced under four criteria: a life’s sentence, a serious terrorist sentence, an extended determinate sentence and a sentence for offenders of particular concern. Grierson also discusses the longer punishments which will be increased for some terrorist offences, including membership in and support of a proscribed organisation. Finally, Grierson reports on the bill’s tougher tools for monitoring suspects, expanding the terrorism prevention and investigation measures. These include the lowering of proof needed for imposing the measures, removing the maximum length these measures can last, and adding new ones. (Grierson, the Guardian, 20.05.2020)
For any questions, please get in touch via:
contact@techagainstterrorism.org